This week I tested Authentec Eikon II fingerprint scanner.  The Authentec Eikon II is a finger print scanner that is supported by Linux. The device is also available under the name “UPEK Eikon II” since the company UPEK has been bought by AuthenTec in September 2010 and sells the UPEK products under the new brand. The scanner is supported by the fprint [1] software under Linux, which provides several finger print scanners. Alternatively, the program FingerPrint GUI can be used. This program provides a graphical interface for the scanner and enables the X-Server loging under GDM per finger scan. The PAM module “libpam_fingerprint.so” is necessary for this.
The Authentec Eikon II is a finger print scanner that is supported by Linux. The device is also available under the name “UPEK Eikon II” since the company UPEK has been bought by AuthenTec in September 2010 and sells the UPEK products under the new brand. The scanner is supported by the fprint [1] software under Linux, which provides several finger print scanners. Alternatively, the program FingerPrint GUI can be used. This program provides a graphical interface for the scanner and enables the X-Server loging under GDM per finger scan. The PAM module “libpam_fingerprint.so” is necessary for this.
Installation
Connect your device and find it listed and connected
root@client:/var/log# lsusb Bus 001 Device 041: ID 80ee:0021 VirtualBox USB Tablet Bus 001 Device 040: ID 8086:0189 Intel Corp. Bus 001 Device 043: ID 147e:2016 Upek Biometric Touchchip/Touchstrip Fingerprint Sensor Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Install requested libraries:
sudo add-apt-repository ppa:fingerprint/fprint sudo apt-get update sudo apt-get install libfprint0 libpam-fprintd fprint-demo gksu-polkit libusb-dev
Then start our dbus with command
service dbus start
If dbus is not started, you will see following error :
** (fprintd:28497): WARNING **: Failed to open connection to bus: Failed to connect to socket /var/run/dbus/system_bus_socket: No such file or directory
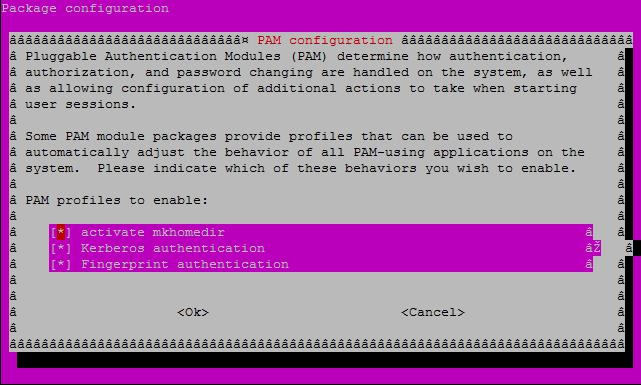
Update authentication methods:
sudo pam-auth-update
Following commands are supported:
sudo fprintd-enroll [username] – Save your fingerprint sudo fprintd-verify [username] – Verify your fingerprint sudo fprintd-list [username] – List of saved fingeprints sudo fprintd-delete [username] – Delete user’s fingerprint
How fingerprint authentication works
When you set up fprintd and enroll your fingerprint for the first time, the scan (basically just an image) gets saved on your hard drive (it goes into /var/lib/fprint/<username>). Then when you try to authenticate yourself, the system gets another scan from reader, and it checks whether the picture received looks more or less the same as the picture stored on disk. If that is the case, the user is let in. This implies that the fingerprint authentication cannot serve as a source of any secret data that could then be used as a password (to decrypt the content of the default keyring or to unlock encrypted partitions, for instance). Theoretically, one could think of a mathematical reduction of the fingerprint to a number, a reduction that would be comprehensive as well as consistent so that different scans of the same finger always be reduced to the same number but scans of different fingers produce different numbers. Then only a hash of such a description of the fingerprint pattern could be saved on disk for the sake of authentication, and the number itself could be used as a secret, not a particularly strong secret since you keep it publicly at a well known place (your fingertip) and keep leaving copies of it on everything you touch, but at least it wouldn’t be stored on your disk, and it could be used for decrypting the keyring, for instance. However, such a technology is not available at the moment, and it doesn’t seem to be feasible either. One hundred years of forensic dactyloscopy haven’t brought any applicable algorithm. For the time being, one has to settle for fingerprints only as means of authentication, not as source of passwords for decrypting one’s enciphered content. [1]
Literature
[1] LaunchPad, “‘Fingerprint readers integration’ team.”[Online]. Available: https://launchpad.net/~fingerprint/+archive/fprint.